Blog Center
Explore the latest stories and insights!

What are the HIPAA Security Rule Safeguards
Date: 2022/10/19
HIPAA | 4.55 MIN READ
This blog post covers what you need to know about the HIPAA Security Rule safeguards. Here’s what you will learn by reading:
➔ What the HIPAA Security Rule is and its importance
➔ Flexibility of the HIPAA Security Rule
➔ Goals of the HIPAA Security Rule
➔ What protected health information (PHI) is protected
➔ Addressable specifications and how to decide which ones to implement
➔ Importance of HIPAA risk assessments
➔ Details about the HIPAA Security Rule safeguards
What is the HIPAA Security Rule?
The Security Rule is a part of the Health Insurance Portability and Accountability Act (HIPAA). It applies only to electronic Protected Health Information (ePHI). The HIPAA Security Rule outlines regulations to protect against breaches of ePHI. Covered entities must abide by the Security Rule. HIPAA-covered entities include health plans, clearing houses, and health care providers. The Centers for Medicare & Medicaid Services has a free tool to help you figure out if your practice is a covered entity.
What is the importance of the Security Rule?
Technology is always advancing. It makes it easier for healthcare employees to access patient records. But technology poses a serious security risk. The Security Rule is important to protect your patients and your practice. ePHI is very valuable. A breach can negatively affect a patient for life. It can affect their finances, as well as their medical care. Breaches also impact your practice. A HIPAA fine can be as high as $1.5 million in a given year.
Is the Security Rule flexible with changing technology?
The Security Rule is designed to be “ technology-neutral .” It facilitates the use of the latest and best technologies. The standards within the Security Rule do not require specific protective technologies. Instead, it gives practices technological freedom when it comes to meeting standards.
What are the goals of the Security Rule?
The law consists of technical, physical, and administrative safeguards. These safeguards have been put in place to:
- Restrict unauthorized access to ePHI
- Audit who, how, and when ePHI is accessed
- Ensure that ePHI is not altered or destroyed inappropriately
- Make sure people are who they say they are
- Prevent unauthorized disclosures of ePHI
What PHI is protected?
These are the different types of data that covered entities must keep secure:
- Data in motion: data moving through a network
- Data at rest: data that is kept in databases, servers, flash drives
- Data in use: data that is being created, retrieved, updated, or deleted
- Data disposed: data that has been discarded
Are addressable specifications optional?
If an implementation specification is “required,” it must be implemented. But are addressable specifications optional? No. Addressable specifications do allow for flexibility, though. In meeting addressable specifications, a covered entity will do one of the following:
- Put in place the addressable specification
- Implement one or more alternative security measures to accomplish the same purpose
- Not implement either an addressable specification or an alternative
The covered entity must document their choice. But cost alone is not a sufficient reason to not implement a safeguard.
How do I decide what addressable specifications to implement?
Covered entities must perform a HIPAA risk assessment. The risk assessment helps the covered entity determine whether:
- An addressable specification should be implemented
- An alternative exists
The covered entity must document:
- The results of the risk assessment
- Any decisions made about addressable specifications
Why perform a HIPAA risk assessment?
The risk assessment is a requirement under HIPAA. The risk assessment objective is to identify potential risks and vulnerabilities of ePHI. A covered entity is required to protect any ePHI that their organization creates, receives, maintains, or transmits.
What are the three Security Rule safeguards?
These Security Rule safeguards ensure the confidentiality, integrity, and security of ePHI.
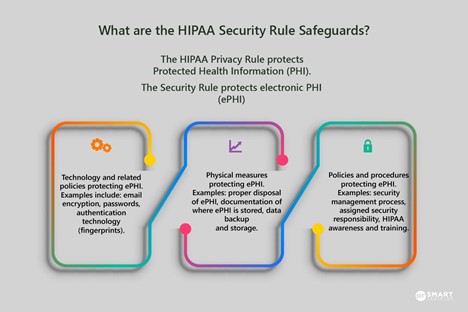
Technical Safeguards
These are technical security measures that guard against unauthorized access to ePHI. Technical safeguards focus on technology. These safeguards consist of access controls, audit controls, integrity controls, and transmission security.
Access Controls: Put policies and procedures in place that assure only authorized employees have access to ePHI.
Audit Controls: Use hardware and software to record and monitor access to systems that continue ePHI.
Integrity Controls: Put procedures in place to ensure ePHI is not altered, destroyed, or tampered with.
Transmission Security: Have security measures that protect against unauthorized access to ePHI being transmitted electronically.
Physical Safeguards
These safeguards relate to the physical security of data, as well as who has access to where it is stored. Practices need to protect physical computer systems, as well as servers and buildings from natural disasters and hacking. The physical safeguards also address workstation and device security. Physical safeguards are made up of access controls, workstation use and security, and device and media controls.
Access Controls: Procedures that limit physical access to computers and servers.
Workstation Use and Security: Procedures that protect the workstation and computer from authorized use.
Device and Media Controls: Policies for devices that contain ePHI, and how they can be removed from a facility.
Administrative Safeguards
Administrative safeguards require that a Privacy Officer is designated to identify and analyze potential risks to the integrity of ePHI. The Privacy Officer must implement security measures to reduce the risk of breaches. Administrative safeguards include a security management process, security personnel, information access management, and workstation security and awareness.
Security Management Process: Implement security measures to reduce security vulnerability. A key aspect of this is the HIPAA risk assessment.
Security Personnel: Assign a Privacy Officer.
Information Access Management: Assure only appropriate employees have access to ePHI, and only in appropriate times.
Workstation Security and Awareness: Implement annual training, education on your security procedures, and sanctions for employees who violate these security procedures.
Is your Practice HIPAA Compliant?
Smart Training has informative training modules to help employees comply with HIPAA. For example, HIPAA 101 and a training for your Privacy Officer. But if you need more HIPAA help, Smart Training’s Dental Platinum+,ental Essentials, and Complete Medical Compliance packages are a more comprehensive HIPAA solution. Including HIPAA training, HIPAA policies and procedures, risk assessment, and up-to-date HIPAA documents. Request a free demonstration with a Compliance Adviser. If HIPAA is a challenge, Smart Training can help you with your compliance needs.
Subscribe to Our Blog